Have you conducted your security risk analysis yet?
The security risk analysis is critical to making sure your organization is protecting patient data in compliance with the requirements in the HIPAA Security Rule. Plus, you have to conduct an SRA by the end of 2019 if you’re participating in the Medicare Promoting Interoperability Program.
This SRA series will cover 8 steps designed to help you identify, prioritize, and address risks to your data. Throughout this series, we’ll give examples of how you can organize your SRA and prepare yourself to strengthen your security posture.
In the last post, we looked at the first two steps of the SRA, so catch up on that first if you need to.
This blog post will guide you through steps 3 and 4 of the security risk analysis: identifying potential vulnerabilities and identifying realistic threats.
Important Definitions
- Vulnerability. A flaw or weakness in system security procedures, design, implementation, or internal controls that could be exploited, either accidentally or intentionally, and result in a security breach or violation of an organization’s security policies.
- Technical vulnerabilities:
 Holes, flaws, and weaknesses in the development of information systems
Holes, flaws, and weaknesses in the development of information systems- Incorrectly configured/implemented systems (for example, cloud misconfigurations)
- Lack of technical safeguards (for example, poor password management or insufficient antimalware)
- Nontechnical vulnerabilities:
- Ineffective or non-existent security policies, procedures, standards, or guidelines
- Technical vulnerabilities:
- Threat. The potential for a person or thing to accidentally trigger or intentionally exploit a specific vulnerability (for example, a hacker cracking a weak password).
- Types of threats (more about threat sources below):
- Natural
- Human
- Environmental
- Where threats occur:
- Information systems
- Operating systems
- Physical environment
- Types of threats (more about threat sources below):
3. Identify Potential Vulnerabilities
The third step of your SRA is to develop a list of vulnerabilities that could be exploited by a threat source. Vulnerabilities are realistic technical and nontechnical areas where electronic protected health information (ePHI) could be disclosed without proper authorization, improperly modified, or made unavailable.
For example, if a workstation isn’t set to automatically log off after a period of inactivity, this is a vulnerability. An unauthorized person could access the workstation (and the sensitive data it contains) while the employee is away from their desk.
Resources for identifying technical vulnerabilities include:
- A vulnerability scanning tool (such as RapidFire, which is what we use).
- The National Vulnerability Database. Keep in mind this isn’t a complete software listing and may not include many of the software used in healthcare.
Once you compile a list of your vulnerabilities, rank them according to how likely it is that they could be exploited, whether unintentionally or intentionally.
4. Identify Realistic Threats
Next, develop a list (called a threat statement) of potential threat sources related to the operating environment.
Threat sources are the realistic and probable human and natural incidents that can have a negative impact on your organization’s ability to protect ePHI. Threat sources can be natural, human, or environmental.
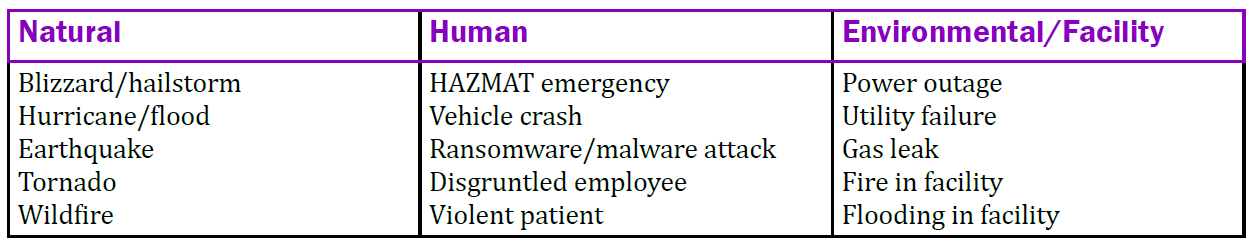
Threat modeling is a method of identifying security threats. Threat models help you manage risks after you complete your risk analysis. Use a threat model, such as STRIDE or DREAD, to get a complete and accurate picture of potential threats (see below).
STRIDE Model
The STRIDE model helps you identify computer security threats by dividing them into 6 categories:
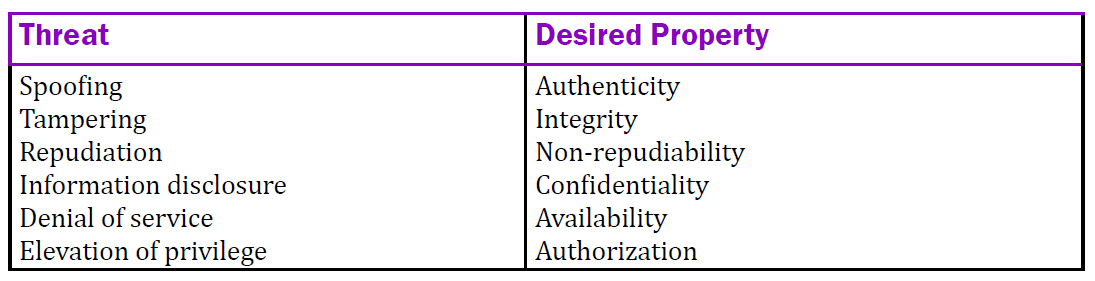
DREAD Model
The DREAD model also helps you assess the risk of computer security threats:
- Damage. How bad would an attack be?
- Reproducibility. How easy is it to reproduce the attack?
- Exploitability. How much work is it to launch the attack?
- Affected users. How many people would be impacted?
- Discoverability. How easy is it to discover the threat?
Give each category a rating from 1 to 10. This rating helps you decide which issues to prioritize.
In addition to threat modeling, you can use the NIST Special Publication 800-30 Guide for Conducting Risk Assessments. Use the NIST tables below to assign likelihood (in percentage and low/medium/high) to a threat event’s initiation, occurrence, and impact.
For example, if you find that a threat being initiated or occurring would almost certainly have adverse impacts on your organization or data, that particular threat would have a very high likelihood of adversely impacting your organization (see Table G-4 below).
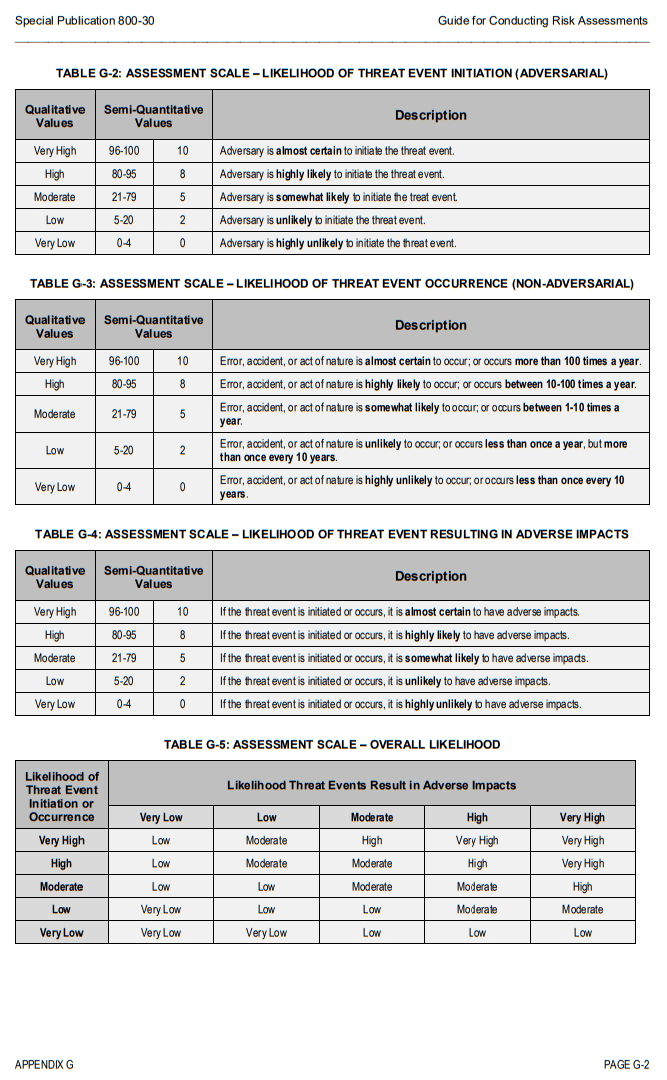
In this stage of your security risk analysis, it’s important to put together a comprehensive list of your vulnerabilities and potential threat sources. In this list or spreadsheet, you’ll want to determine the likelihood of threat sources exercising your vulnerabilities and what impact that would have.
This helps you understand the level of risk and how much damage you’d face should a threat event occur. Knowing this, you’ll be able to prioritize risks to mitigate after you complete the SRA and develop a risk management plan.
Our HIPAA experts can conduct your security risk analysis for you. To learn about our SRA service and methodology, contact us at support@hipaatrek.com.
Stay tuned for next week’s blog post, which will cover steps 5 and 6: assessing security controls and assessing risk impact.

Are you up to date with HIPAA?
Check out our cheat sheet for staying up to date with changing regulations!
READ MORE: Your Security Risk Analysis in 2019: Tips and Tools












